🤺 Defeating Anti-forensics Techniques
Anti-forensics refers to various techniques by cybercriminals to destroy or conceal traces of illegal activities and obstruct forensic investigation processes. After compromising a system, attackers frequently attempt to destroy or conceal all traces of their activities, making forensic investigation extremely difficult for investigators. Anti-forensics must be overcome/defeated by forensic investigators so that an analysis yields concrete and accurate evidence that can be used to identify and prosecute the perpetrators.
5.1 Understand Anti-Forensics Techniques
- What is Anti Forensics?
- Anti-forensics (also known as counter forensics) is a common term for a set of techniques aimed at complicating or preventing a proper forensics investigation process
- Goals
- Interrupt and prevent information collection
- Making it difficult for the investigator to find evidence
- Hide traces of crime or illegal activity
- Compromise the accuracy of a forensics report or testimony
- Delete evidence that an anti-forensics tool has been run
- Anti-forensics Techniques
- Data/File Deletion
- Password Protection
- Steganography
- Data Hiding in File System Structures
- Trail Obfuscation
- Artifact Wiping
- Overwriting Data/Metadata
- Encryption
- Program Packers
- Minimizing Footprints
5.2 Discuss Data Deletion and Recycle Bin Forensics
- Anti-forensics Techniques: Data/File Deletion
- When a file is deleted from the hard drive, the pointer to the file gets deleted but the contents of the file remains on the disk
- In other words, the deleted files can be recovered from the hard disk until the sectors containing the contents of the file are overwritten with the new data
- Data recovery Tools such as Autopsy, Recover My Files, Eas US Data Recovery Wizard and R-Studio can be used for recovering deleted files and folders
- What Happens When a File is Deleted in Windows?
- FAT File System
- The OS replaces the first letter of a deleted file name with a hex byte code: E5h
- E5h is a special tag that indicates that the file has been deleted
- The corresponding cluster of that file in FAT is marked as unused, although it will continue to contain the information until it is overwritten
- NTFS File System
- When a user deletes a file, the OS just marks the file entry as unallocated but does not delete the actual file contents
- The clusters allocated to the deleted file are marked as free in the $BitMap ($BitMap file is a record of all used and unused clusters)
- The computer now notices those empty clusters and avails that space for storing a new file
- The deleted file can be recovered if the space is not allocated to any other file
- FAT File System
- Recycle Bin in Windows
The Recycle Bin is a temporary storage place for deleted files
The file remains in the Recycle Bin until you empty the Recycle Bin or restore the file
Items can be restored to their original positions with the help of the Restore all items option of the Recycle Bin
Recycle Bin storage location on FAT file system:
- FAT file systems (Windows 98 and prior) - Drive:\RECYCLED
Recycle Bin storage location on NTFS file system:
- Windows 2000, NT and XP - Drive:\RECYCLER\
- Windows Vista and later versions - Drive:\$Recycle.Bin\
- Windows 2000, NT and XP - Drive:\RECYCLER\
When a file is deleted, the file’s complete path and its name are stored in a hidden file called INFO2 (Windows 98) in the Recycled folder. This information is used to restore the deleted files to their original locations.
Prior to Windows Vista, a file in the Recycle Bin was stored in its physical location and renamed using the syntax:
- D
<#>. - “D” = deleted
- Example:
- De7.doc = File deleted from E: drive, “eighth” file received by recycle bin, and “doc” file
- D
Windows Vista and later versions:
- Syntax:
- $R<#>.
, “#” represents a set of random letters and numbers
- $R<#>.
- Metadata file:
- $I<#>.
, “#” represents a set of random letters and numbers - Contains:
- Original file name
- Original file size
- Date and time of deletion
- $I<#>.
- $R and $I files are located at: C:\$Recycle.Bin\
\
- Syntax:
- Recycle Bin Forensics
- Original files pertaining to the $I files are not visible in the Recycle Bin folder when,
- $I file is corrupted or damaged
- Attacker/Insider deletes $I files from Recycle Bin
- During a forensic investigation, the investigator should check for the $R files in the Recycle Bin directory to counter the anti-forensic technique used by the attacker

- If the metadata files related to the original files are not present in the folder, then the investigator can use the ‘copy’ command to recover the deleted files ($R files)
- copy <$R(or Filename)>
* 

- copy <$R(or Filename)>
- Original files pertaining to the $I files are not visible in the Recycle Bin folder when,
5.3 Illustrate File Carving Techniques and Ways to Recover Evidence from Delted Partitions
- File Carving
- Technique to recover files and fragments of files from the hard disk in the absence of file system metadata
- File identification and extraction is based on certain characteristics such as file header or footer rather than the file extension or metadata
- A file header is a signature (AKA magic number), which is a constant numeric or text value that determines a file format
- Example:
- A suspect may try to hide an image from being detected by investigators by changing the file extension from .jpg to .dll
- However, changing the file extension does not change the file header, and analysis tells the actual file format
- A file format is confirmed as .jpg if it shows “JFIF” in the file header and hex signature as “4A 46 49 46”
- Example:
- Investigators can take a look at file headers to verify the file format using tools such as 010 Editor, CI Hex Viewer, Hexinator, Hex Editor Neo, Qiew, WinHex, etc.
- Note: File carving does not require the file system structure to recover data from the disk whereas File Recovery requires knowledge of the file system structure to recover deleted data
- File Carving on Windows
Windows tracks its files/folders on a hard drive using the pointers that tell the system where the file begins and ends
When a file is deleted from the hard drive, the pointer to the file gets deleted but the contents of the file remain on the disk
The deleted files can be recovered from the hard disk until the sectors containing the contents of the file are overwritten with new data
File carving in SSDs are different from HDDs since files deleted from the TRIM (enabled by default) cannot be recovered
- SSD File Carving on Windows File System
- When a forensic investigator performs file carving on a forensic image file acquired from a TRIM enabled SSD, it is not possible to recover deleted data from the disk
- Tools such as Autopsy, EaseUS Data Recovery, etc., can be used to carve data from the disk
- When Autopsy is employed to perform file carving on an evidence file, the software lists the file names but the deleted data cannot be recovered

- When performing data acquisition, the investigator should check the status of the SSD’s TRIM feature
- In TRIM disabled SSD’s, the forensic investigator can perform file carving to recover lost data from the drive

- HDD File Carving on Windows File System
- Forensic Image files can be acquired using tools such as FTK Imager, DD utility, and examined using Autopsy
- Autopsy recovers the deleted data from the evidence file

- File Recovery Tools: Windows
- Recover My Files
- Recovers deleted files emptied from the Windows Recycle Bin, including files lost due to formatting or reinstalling a hard drive, or files removed by a virus, Trojan, unexpected system shutdown, or software failure

- EaseUS Data Recovery Wizard
- Recovers lost data due to deleting, formatting, partition loss, OS crash, virus attacks, etc.

- Recover My Files
- File Carving on Linux
When a file is deleted from Linux using the command /bin/rm/, the inode pointing to the file gets removed but the file remains on the disk until it is overwritten with new data
If a running process keeps a file open and then removes the file, the file contents are still on the disk, and other programs will not reclaim the space
The second extended file system (ext2) is designed in such a way that it shows several places where data can be hidden
It is required to note that if an executable erases itself, its contents can be retrieved from a /proc memory image.
- The command cp /proc/$PID/exe/tmp/file creates a copy of a file in /tmp
Third-party tools such as Stellar Pheonix Linux Data Recovery, R-Studio for Linux, Test Disk, PhotoRec, and Kernel for Linux Data recovery can be used to recover deleted files from Linux
- SSD File Carving on Linux File System
- Forensically acquired data from a TRIM disabled SSD should be examined using tools such as Autopsy, R-Studio, etc.
- In Autopsy, the carved data from the evidence file is displayed under the appropriate data source with the heading “$CarvedFiles”

- File Carving on macOS
- SSD File Carving on Apple File System
- Same as other files systems, using disk recovery tools such as R-Studio

- Recovering Deleted Paritions
The MBR partition table contains the records of the primary and extended partitions of a disk
When a partition is deleted from a disk, the entries with respect to deleted portion are removed by the computer from the MBR partition table
Investigators use tools such as R-Studio and EaseUS Data Recovery Wizard to scan the disk from lost partitions and recover them
These automated tools perform full disk scans, looking for deleted partition information and reconstructing the portion table entry for deleted partition
- Using R-Studio
- When a portion is deleted from a drive, the partition is marked as Unallocated in Disk Management
- The perpetrator merges the unallocated portion with the system’s primary portion (or existing partition) to make it difficult for the investigator to identify the lost partition
- In this scenario, the investigator should use automated tools such as R-Studio to retrieve the lost portion of data
- R-Studio is a data recovery tool for Windows, Linux, and Mac that can recover partitions that are deleted, damaged or formatted


- Using EaseUS Data Recovery Wizard
- Similar to R-Studio, EaseUS Data Recovery Wizard recovers data from FAT and NTFS based file system partitions


5.4 Explore Password Cracking/Bypassing Techniques
- Anti-forensics Technique: Password Protection
- While conducting forensic investigation on suspect’s computer, accessing password protected resources is on of the challenges faced by the investigator
- Investigators can use password cracking tools such as Ophcrack and Rainbow Crack to circumvent the password protection
- Password Types
- Cleartext Passwords
- Transmitted or stored on media without any encryption
- Obfuscated passwords
- Passwords are encrypted using an algorithm and can be decrypted by applying a reverse algorithm
- Password Hashes
- Password hashes are signatures of the original password, generated using a one-way algorithm. Password hashed using hash algorithms (MDS, SHA, etc.) are not reversible
- Cleartext Passwords
- Password Cracking Techniques
- Dictionary Attack
- Dictionary file is loaded into the cracking application that runs against user accounts
- Brute Forcing Attacks
- The program tries every combination of characters until the password is broken
- Rule-based Attack
- Attack is used when some information about the password is known.
- Dictionary Attack
- Using Rainbow Tables to Crack Hashed Passwords
Rainbow Table
- A rainbow table is a precomputed table that contains word lists in the form of dictionary files and brute force lists and their hash values
Compare Hashes
- Capture the hash of a password and compare it with the precomputed hash table. If a match is found, then the password is cracked.
Easy to Recover
- Easy to recover passwords by comparing captured password hashes to precomputed tables
- Tool to Create Rainbow Tables: Winrtgen
- Winrtgen is a graphical Rainbow Tables Generator that supports LM, FastLM, NTLM, LMCHALL, HalfLMCHALL, NTLMCHALL, MSCACHE, MD2, MD4, MD5, SHA1, RIPEMD160, MySQL323, MySQLSHA1, CiscoPIX, ORACLE, SHA-2 (256), SHA-2 (384), and SHA-2 (512) hashes

- Password Cracking: Using L0phtCrack and Ophcrack
- L0phtCrack
- L0phtCrack is a password auditing and recovery application packed with features such as scheduling, hash extraction from 64-bit Windows versions, and networks monitoring and decoding

- Ophcrack
- Ophcrack is a Windows password cracker based on rainbow tables. It comes with a Graphical User Interface and runs on multiple platforms.

- L0phtCrack
- Password Cracking: Using Cain & Abel and RainbowCrack
- Cain & Abel
- It allows recovery of various kinds of passwords by sniffing the network, cracking encrypted passwords using dictionary attacks, brute-force attacks, and cryptanalysis attacks

- RainbowCrack
- RainbowCrack cracks hashes with rainbow tables. It uses a time-memory tradeoff algorithm to crack hashes

- Cain & Abel
- Password Cracking: Using PwDump7
- PwDump7 extracts LM and NTLM password hashes of local user accounts from the database

- Bypassing Passwords on Powered-off Computer
- Bypassing BIOS Passwords
- BIOS (Basic Input Output System) is a firmware code run by a system when powered on. It is a type of boot loader.
- The main function of BIOS is to identify and initialize system component hardware (such as hard disk, video display card, and other motherboard components)
- The procedure to bypass BIOS password depends on the manufacturer
- In the BIOS setup, there are three types of passwords
- System Password
- Admin Password
- HDD Password
- Note: Bypassing BIOS password can unlock System and Admin password but not the HDD password
- Methods to Bypass/Reset BIOS password
- Using a manufacturer’s backdoor password to access the BIOS
- Using password cracking software
- Resetting the CMOS using jumpers or solder beads
- Removing the CMOS battery for at least 10 minutes
- Bypassing BIOS Passwords by Resetting CMOS Using Jumpers
- Resetting CMOS using Jumpers
- By adjusting the jumpers or dipswitches on a motherboard, all custom settings, including BIOS passwords (System and Admin passwords), will be cleared
- Check the computer or motherboard manufacturer’s documentation to locate the jumpers/dip switches
- If the documentation is not available, by default the jumper position is across pins 1 and 2
- Steps involved in bypassing BIOS Password:
- Shut down the system and unplug the power cord
- Move the jumper from its default position so that it is across pins 2 and 3; this clears the BIOS/CMOS settings
- Now, turn on the machine to verify that the password has been reset
- If the password is cleared, turn off the computer and return the jumper to its original position
- Resetting CMOS using Jumpers
- Bypassing BIOS Passwords by Removing CMOS Battery
- Shut down the system and disconnect the power plug
- Open the CPU cabinet and locate the CMOS battery (silver circular battery) on the motherboard
- Remove the CMOS battery from the socket and keep it out for 20 to 30 minutes. This flushes out the CMOS memory that stores BIOS passwords and other configurations.
- Replace the battery and start the system normally
- Tool to Reset Admin Password: Lazesoft Recover My Password
- Lazesoft Recover My Password tool creates a bootable CD/USB that can be used to reset/unlock Windows user passwords when the login credentials of the account are lost
- When an organization’s best practices include or an individual contains a CD/USB drive burned with user password recovery tools, the investigator should make use of those CD/USB drives to crack the user password


- Bypassing Windows User Password Using Lazesoft Recovery Suite
- Boot the machine to the USB Boot Drive and Select “Lazesoft Recovery Suite to load the utility”. Click on “Password Recovery”
- Select “Reset Windows Password”. Click “Next”.
- Select Windows Installation to be unlocked from the list. For example, Microsoft Windows 10 x64 Edition. Click “Next” to get the User accounts list
- Select the “User Account’’ to be unlocked. Click “Next’’
- Click the “Reset/Unlock” button to unlock the selected User account password
- Now, click “Reboot” option to restart the machine and the OS loads without prompting for a user password
- Boot the machine to the USB Boot Drive and Select “Lazesoft Recovery Suite to load the utility”. Click on “Password Recovery”
- Bypassing Windows User Password Using Booting Live CD/USB
- Boot the machine from the Live CD/USB (here, CAINE LIVE CD/DVD is used) to get access to the machine’s hard disk and its contents


5.5 Detect Steganography, HIdden Data in File System Structures, Trail Obfuscation, and File Extension Mismatch
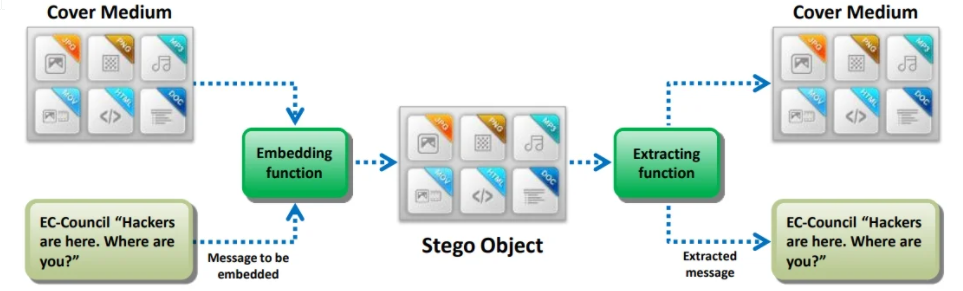
- Anti-forensics Technique: Steganography
Seganography is a technique of hiding a secret message within an ordinary message and extracting it at the destination to maintain confidentiality of data
Utilizing a graphic image as a cover is the most popular method to conceal data in files
The attacker can use steganography to hide messages such as a list of the compromised servers, source code for the hacking tool, and plans for future attacks
The forensic investigator examines the Stego-Object to extract the hidden information
- Defeating Anti-forensics: Steganalysis
- Steganalysis is the art of discovering and rendering covert messages using steganography
- It detects the hidden messages embedded in images, text, audio, and video carrier mediums using steganography
- Challenges of Steganalysis
- Suspect information stream may or may not have encoded hidden data
- Efficient and accurate detection of hidden content within digital images is difficult
- The message might have been encrypted before inserting into a file or signal
- Some of the suspect signals or files may have irrelevant data or noise encoded into them
- Steganalysis Methods/Attacks on Steganography
- Stego-only
- Only the stego object is available for analysis
- Known-stego
- The attacker has access to the stego algorithm and both the cover medium and the stego-object
- Known-message
- The attacker has access to the hidden message and the stego object
- Known-cover
- Attacker compares the stego-object and the cover medium to identify the hidden message
- Chosen-message
- Generates stego object from a known message using specific steganography tools in order to identify the steganography algorithms
- Chosen-stego
- The attacker has access to the stego-object and stego algorithm
- Chi-square
- The attacker performs probability analysis to test whether the stego object and original data are the same or not
- Distinguishing Statistical
- The attacker analyzes the embedded algorithm used to detect distinguishing statistical changes along with the length of the embedded data
- Blind Classifier
- A blind detector is fed with the original or unmodified data to learn the resemblance of original data from multiple perspectives
- Stego-only
- Detecting Steganography (Text, Image, Audio, and Video Files)
- Text File
- For the text files, the alterations are made to the character positions for hiding data
- The alterations are detected by looking for text patterns or disturbances, language used, and an unusual amount of blank spaces
- Image File
- The hidden data in an image can be detected by looking for changes in size, file format, metadata, and color palette pointing to the existence of the hidden data
- The statistical analysis method is used for image scanning
- Audio File
- Statistical analysis method can be used to detect audio steganography as it involves LSB (Least Significant Bit) modifications
- The inaudible frequencies can be scanned for hidden information
- The odd distortions and patterns in the audio graph indicate the existence of the secret data
- Video File
- Detection of the secret data in video files includes a combination of methods used in image and audio files
- Text File
- Steganography Detection Tools
- zsteg
- zsteg tool is used to detect stegano-hidden data in PNG and BMP image files

- Other Tools
- StegoVeritas, Stegextract, StegoHuntTM, Steganography Studio, Virtual Steganographic Laboratory (VSL)
- zsteg
- Defeating Anti-forensics Technique: Detecting Data Hiding in File System Structures Using OSForensics
- Host Protected Areas (HPA) and Device Configuration Overlay (DCO) are hidden areas on the hard drives
- The perpetrator with malicious intent make use of these hidden areas to hide illegal data
- Data hidden in these areas are not accessible to the BIOS or OS
- Forensic tools such as OSForensics can be used to detect and create a forensic image of the DCO and HPA hidden areas

- Anti-forensics Technique: Alternate Data Streams
Attackers use Alternate Data Streams (ADS) to hide data in Windows NTFS and cannot be revealed through command line or Windows Explorer
ADS allows the attacker to hide any number of streams into one single file without modifying the file size, functionality, etc., except the file date
However, the file date can be modified using anti-forensics tools like TimeStomp
In some cases, these hidden ADS can be used to remotely exploit a web server
- Defeating Anti-forensics Technique: Detecting Alternate Data Streams
- Step 1:
cdto the directory where you want to search hidden data streams and execute the following command to search for ADS in the hard drivegci -recurse | % { gi $_.FullName -stream * } | where stream -ne ':$Data'
- Step 2:
Look into the actual directory to find the files that contains ADS; For example, simple_file1.txt and simple_file2.txt, each of size 38 bytes contain hidden data streams

when opened displays data in it but hidden alternate data streams cannot be viewed via Windows Explorer

- Step 3:
Using Command Prompt,
cdto the directory where hidden data streams are found and run the following command:notepad filename.extension:streamname.extension

- Step 1:
- Defeating Anti-forensics Technique: Detecting Alternate Data Streams Using Stream Detector
- Stream Detector is a forensic tool that identifies all hidden files such as images, videos, text, and executables within Alternate Data Streams present on NTFS drives
- It can detect the hidden streams on the actual file directory and list the file name, type, size of the stream, etc.
- This tool can be used to detect and extract hidden streams, delete the file and unwanted streams

- Anti-forensics Technique: Trail Obfuscation
- The purpose of trail obfuscation is to confuse and mislead the forensics investigation process
- Attackers mislead investigators via log tampering, false e-mail header generation, timestamp modification, and various file headers’ modification
- Some of the techniques attackers use for data/trail obfuscation:
- Log cleaners
- Spoofing
- Misinformation
- Zombie accounts
- Trojan commands
- Traffic content obfuscation can be attained by means of VPNs and SSH tunneling
- Timestomp is one of the most widely used trail obfuscation tools that allow deletion or modification of timestamp-related information on files.
- Anti-forensics Technique: Detecting File Extension Mismatch Using Autopsy
- Every digital file contains a signature that is located in the first 20 bytes of the file
- In signature analysis, the file header and its extension is compared, and any extension mismatch can be identified
- Autopsy, use “Extension Mismatch Detected” module to identify whether an attempt has been made to tamper the file extension of the known file types
- The mismatched files are listed in the module (as shown in the screenshot) and forensic investigator recovers those files using Autopsy

5.6 Understand Techniques of Artifact Wiping, Overwritten Data/Metadata Detection, and Encryption
- Anti-forensics Technique: Artifact Wiping
- Artifact wiping involves various methods aimed at permanent deletion of particular files or entire file systems
- Disk Wiping Utilities
- Disk wiping involves erasing data from the disk by deleting its links to memory blocks and overwriting the memory contents
- In this process, the application overwrites the contents of MBR, partition table, and other sectors of the hard drive with characters such as null characters or any random character several times (using data wiping standards). In this case, the forensic investigator finds it difficult to recover data from the storage device.
- Some of the commonly used disk wiping utilities include BCWipe Total WipeOut, CyberScrub’s cyberCide, DriveScrubber, ShredIt, etc.
- File Wiping Utilities
- Deletes individual files and file table entries from an OS
- Some of the commonly used file wiping utilities include WipeFile, Freeraser, Eraser, Alternate File Shredder, etc.
- Anti-forensics Technique: Overwriting Data/Metadata
Data overwriting is one of the most common and widely used anti-forensics techniques where perpetrators overwrite all the addressable locations of a digital storage media with some random characters
Standard data wiping tools perform multiple data overwrites on the media rendering any evidence on the media completely unrecoverable using any commercially available tools and processes
Metadata is often more important than the data in order to prove the culpability of a suspect. It helps investigators to create attack timeline, recreate the attack scenes, and fix the ownership of an action or information on the target
Cyber criminals can use different techniques and tools to either completely wipe or manipulate the metadata to avoid and mislead the investigation
Criminals also often use OSes and tools from Live Boot media to avoid any metadata on the target systems
- Defeating Anti-forensics Technique: Detecting Overwritten Data/Metadata
- When a user performs any action on the file, the information pertaining to its creation, modification, and access time alter. This information can be helpful during forensic analysis of the file system.
- When examining MACE times of the files in an NTFS file system, mainly two attributes are analyzed:
- STANDARD_INFORMATION – Contain timestamps modified at user-level
- FILE_NAME - Contain timestamps modified at the system kernel level
- These attributes contain information about:
- CREATION TIME
- LAST ACCESS TIME
- MODIFICATION TIME
- ENTRY MODIFICATION TIME
- To detect timestamp forgery on NTFS file system, the forensic investigator can employ forensic tools such as analyzeMFT to compare $STANDARD INFORMATION and $FILE NAME ATTRIBUTES
- When the $FILE NAME creation date and $STANDARD INFORMATION creation date (for any file) does not match, it indicates that the file has been time stomped
- Anti-forensics Technique: Encryption
Data encryption is one of the commonly used techniques to defeat forensics investigation process
Intruders use strong encryption algorithms to encrypt data of investigative value, which renders it virtually unreadable without the designated key
Additionally, most encryption programs are capable of performing additional functions, including use of a key file, full-volume encryption, and plausible deniability; that makes the investigator’s job more difficult
Cryptanalysis can be used to decrypt encrypted data
- Recover Encrypted Files Using Advanced EFS Data Recovery Tool
- Advanced EFS Data Recovery helps to recover EFS-encrypted files under various circumstances:
- EFS-protected disk inserted into a different PC
- Deleted users or user profiles
- User transferred into a different domain without EFS consideration
- Account password reset performed by system administrator without EFS consideration
- Damaged disk, corrupt file system, or unbootable operating system
- Reinstalled Windows or computer upgrades
- Formatted system partitions with encrypted files left on another disk

- Advanced EFS Data Recovery helps to recover EFS-encrypted files under various circumstances:
5.7 Detect Program Packers and Footprint Minimizing Techniques
- Anti-forensics Technique: Program Packers
Packer is a program used to compress or encrypt the executable programs
Intruders use packers to hide attack tools from being detected through reverse-engineering by modifying the original entry point of the executable
Some of the widely used packers are UPX, BurnEye, Exe Stealth Packer, Smart Packer Pro, etc.
Packed programs that require a password to be run are considered to be strong. Whereas, those that do not require a password are vulnerable to static analysis.
- Unpacking Program Packers
- Consider a scenario where the investigator identifies a packer during forensic investigation
- To unpack/extract the original program executable file from the packer, the investigator should identify the tool used to pack the executable file
- Exeinfo PE tool can analyze the code to identify the packer tool
- To unpack the program packer, use the UPX utility
- upx.exe –d –o [unpacked_file_name] [packer_file_name]

- Anti-forensics Techniques that Minimize Footprint
Use of fake and stolen identities
- Attackers use various identity theft techniques to impersonate others or create fake identities to launch attacks
Running OSes from Live CDs/DVDs/USB
- Attackers can run OSes and attack tools directly from Live CDs/DVDs/USB leaving very minimal or no footprint
Use of virtual machines
- Multiple virtual machines can be spun and destroyed after the attacks with very little effort and cost rendering all the evidence permanently destroyed
Use of cloud services
- Attackers can use cloud infrastructure to host various attack toolkits, launch massive distributed attacks, and destroy it with very less effort, thus making any investigation very difficult
- Defeating Anti-forensics Technique: Detecting USB Devices
- The Microsoft Windows OS records digital forensic artifacts such as timestamps and device information when a USB removable storage device is plugged into the machine
- To enumerate the devices that are connected to the system, use the following command in Windows PowerShell:
- Get-ItemProperty –Path HKLM:\SYSTEM\CurrentControlSet\Enum\USBSTOR\\\ | Select FriendlyName

- The digital artifacts left by the USB removal storage devices are recorded into Windows Registry
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\ USBSTOR\Disk&Ven_[VendorName]&Prod_[ProductName]& Rev_1.00\[SerialNo]

- To check the First Insertion and Last Insertion timestamps of the specific USB device, export the Registry key (specific to a USB device) to the text file
5.8 Understand Anti-forensics Countermeasures
- Anti-forensics Coutnermeasures
- Train and educate the forensic investigators about anti-forensics
- Validate the results of examination using multiple tools
- Impose strict laws against illegal use of anti-forensics tools
- Understand the anti-forensic techniques and their weaknesses
- Use latest and updated CFTs and test them for vulnerabilities
- Save data in secure locations
- Use intelligent decompression libraries to defend against compression bombs
- Replace weak file heuristics with stronger ones










